Introduction
This article will cover creating and deploying an AWS Lambda function using Terraform.
Terraform IaC code allows the deployment of infrastructure to AWS cloud without using AWS CloudFormation. You can access this article's FREE template for download HERE.
What is Terraform?
Terraform is HashiCorp's infrastructure as a code tool. It lets you define resources and infrastructure in human-readable, declarative configuration files, and manages your infrastructure's lifecycle. Using Terraform has several advantages over manually managing your infrastructure:
- Terraform can manage infrastructure on multiple cloud platforms.
- The human-readable configuration language helps you write infrastructure code quickly.
- Terraform's state allows you to track resource changes throughout your deployments.
- You can commit your configurations to version control to safely collaborate on infrastructure.

To deploy infrastructure with Terraform:
- Scope - Identify the infrastructure for your project.
- Author - Write the configuration for your infrastructure.
- Initialize - Install the plugins Terraform needs to manage the infrastructure.
- Plan - Preview the changes Terraform will make to match your configuration.
- Apply - Make the planned changes.
Prerequisites
- An AWS Account
- AWS CLI Configured
- NodeJs
Installing The Terraform
Windows: choco install terraform
Linux: ****sudo apt-get install terraform
Mac OS: brew install hashicorp/tap/terraform
Let’s Start - Create an Empty Project Folder
Create And Upload The Lambda Function Archive
Create File sg-demo/demo.js with below lambda function code
- Lambda Function Code with NodeJs
Create File main.tf with Below Terraform IaC Code Configuration which will define:
- Initialize Providers Plugins
- Provider AWS
- S3 bucket
- S3 Object For Lambda Function Code Archive
Create The Lambda Function And Relevant Resource
Add below Terraform IaC code configuration to main.tf file which will define:
- Lambda Function
- Lambda CloudWatch Log Group
- Lambda Execution IAM Role
- Lambda Execution IAM Role Policy
Create An Output Value For Your Lambda Function's Name
Create file outputs.tf with the below IaC code configuration
Defined Output values are displayed in CLI during executing Terraform commands like apply.
Define Needful Variables
Create file variables.tf with the below IaC code configuration
These defined variables are used within the main.tf file using var.aws_region:
Project Folder Structure At The End
After following the above steps, at the end you will have the below folder structure created:
Project Terraform Initialization
Terraform init prepares the working directory so Terraform can run the configuration.
Terraform downloads the AWS provider and installs it in a hidden subdirectory of your current working directory, named .terraform. The terraform init command prints out which version of the provider was installed. Along with that it also installs other specified plugins like archive, and random.
Terraform also creates a lock file named .terraform.lock.hcl which specifies the exact provider versions used, so that you can control when you want to update the providers used for your project.
Terraform Plan
Terraform plan lets you preview any changes before you apply them.
Terraform Apply
Terraform apply executes the changes defined by your Terraform configuration to create, update, or destroy resources.
Apply the configuration now with the terraform apply command, which will create infrastructure in a specified cloud provider with defined resources.
Before it applies any changes, Terraform prints out the execution plan which describes the actions Terraform will take in order to change your infrastructure to match the configuration.
Terraform will now pause and wait for your approval before proceeding, In this case, the plan is acceptable, so type yes at the confirmation prompt to proceed. After executing the plan it will take a few minutes for your Lambda and relevant resources to get successfully deployed to AWS. Apply command response in CLI show number of resources deployed with outputs items.
That’s It!!! Demo Lambda Successfully Deployed To AWS Using Terraform :)
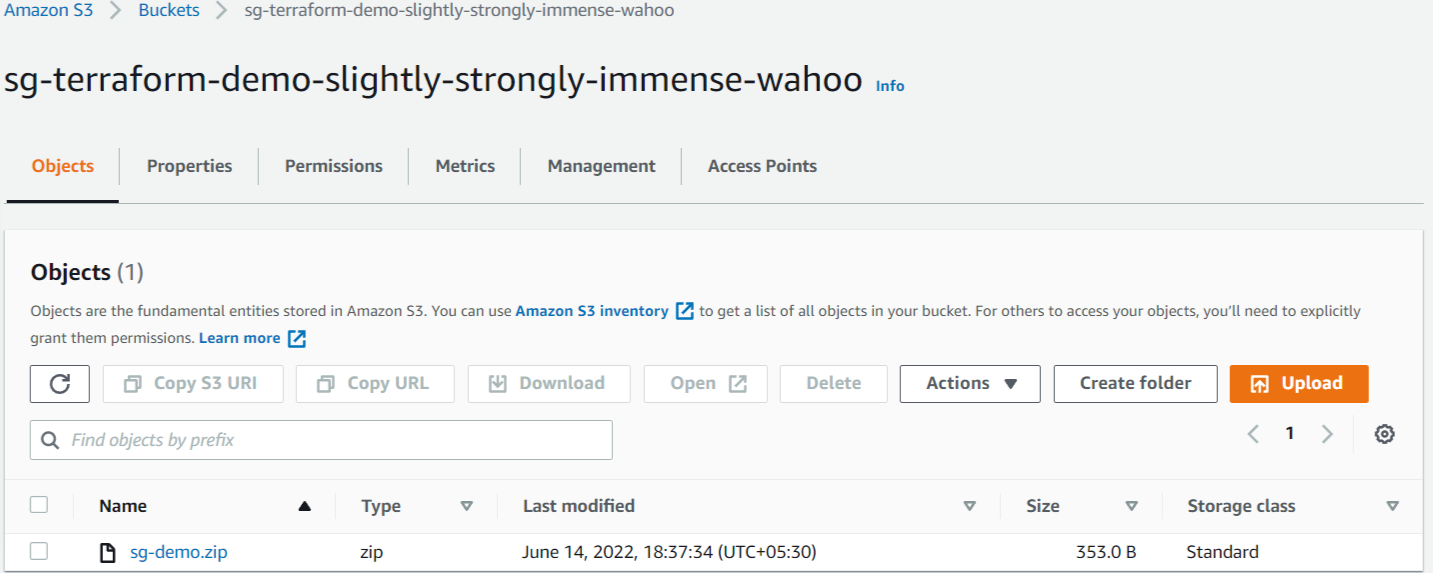
AWS S3 Bucket And Relevant Objects Created
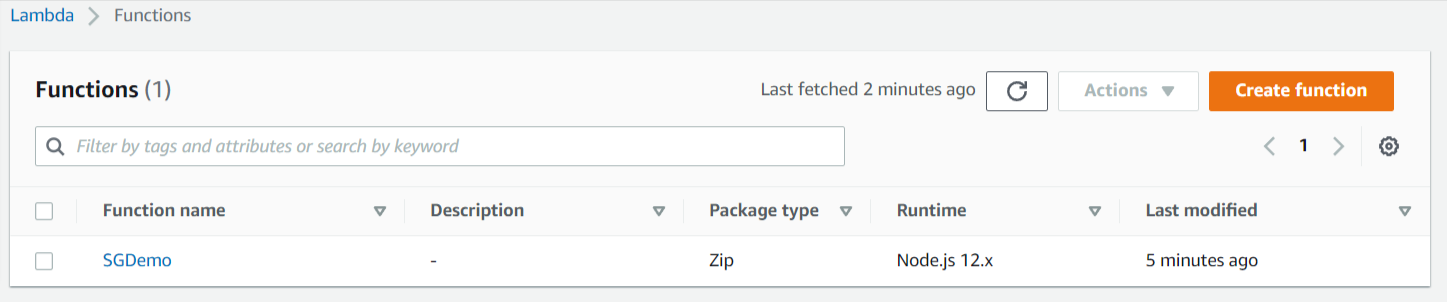
AWS Lambda Function Deployed
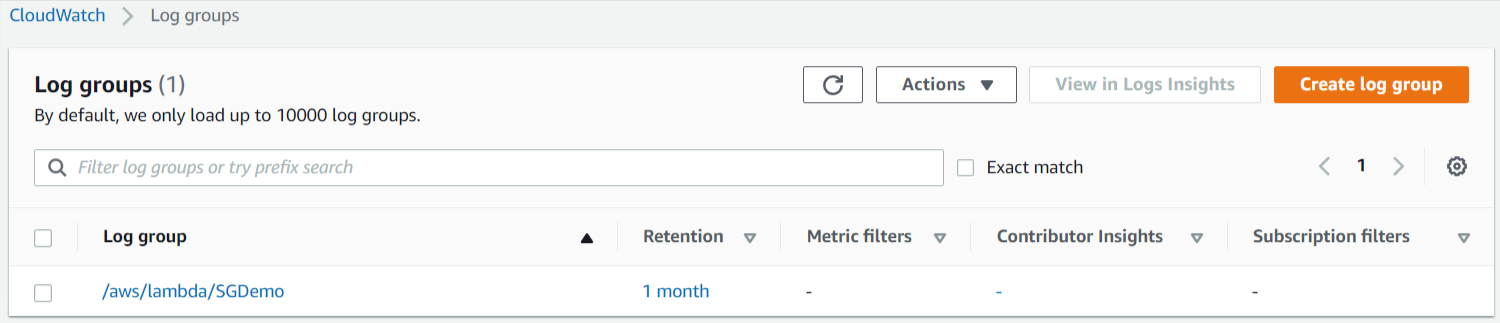
Lambda Function Execution Role Created With Needful Permission

CloudWatch Logs Group Created For Lambda Function
Terraform Destroy
The terraform destroy command terminates resources managed by your Terraform project. This command is the inverse of terraform apply in that it terminates all the resources specified in your Terraform state. It does not destroy resources running elsewhere that are not managed by the current Terraform project.
That’s All Done!!! Now you are ready to get started with the basics of Terraform.
Conclusion
Terraform infrastructure as code allows you to easily create and deploy resources to multiple cloud providers including AWS.
By following this article you will get a basic idea about Terraform CLI commands, Infrastructure as Code configurations, and the basics of deploying the AWS Lambda function that helps you to get started on Terraform.
To explore more about Terraform see these official getting started Terraform documents.






%20(1).svg)

.svg)








.webp)